
Whether it arrives in the form of a flood of obscene pop-up windows assaulting you after a mistyped URL, or malicious code taking over your browser completely, chances are good that every Internet user will be subjected to this practice in some form.
Fortunately, avoiding a browser hijacking is not impossible if you stay aware, and take a few simple precautions. Take the metaphor of locking your car doors while you are out for a drive as an example. If your browser keeps redirecting you to www.anothersiterandomly.com and you are here looking for ways to cure what ails you, i'll cover that too.
To sum it up, I will show you how to avoid and defeat these annoying and potentially embarrassing attacks on your computer, starting with seven preventative measures:
- Use common sense
- Use and update an anti-virus program regularly
- Use antivirus 'auto protection'
- Keep an anti-hijack 'toolkit' for emergencies
- Change your Internet Explorer security settings
- Try an alternate browser
What's a browser Hijacker?
This term covers a range of malicious software. The most generally accepted description for browser hijacking software is external code that changes your Internet Explorer settings. Generally your home page will be changed and new favourites will be added that point to sites of dubious content. In most cases, the hijacker will have made registry changes to your system, causing the home page to revert back to the unwanted destination even if you change it manually.
A browser Hijacker may also disallow access to certain web pages, for example the site of an anti-spyware software manufacturer like Lavasoft. These programs have also been known to disable Antivirus and anti-spyware software.
Most browser hijackers take advantage of Internet Explorer's ability to run ActiveX scripts straight from a web page. Generally, these programs will request permission to install themselves via a popup that loads when you visit a certain site. If you accidentally give them permission to install, IE will execute the program on your computer, changing your settings.
Others may use security holes within Internet Explorer to install themselves automatically without any user interaction at all. Worse, these can be launched from popup ad windows which the user has not even intended to view.
As well as making changes to your home page and other Internet Explorer settings, a hijacker may also make entries to the HOSTS file on your system. This special file directly maps DNS addresses (web URLs) to IP addresses, so every time you typed 'www.google.com' (as an example) you might be redirected to the IP address of a sponsored search or porn site instead.
Some browser hijackers may also install themselves onto your computer system as legitimate programs, leaving an entry in the 'add-remove programs' list in the control panel. There are many faces of broswer hijacking, and to combat the situation, you have to be aware of all the tricks and loopholes that make this scourge possible. Browser hijacking isn't necessarily a virus, and isn't necessarily adware, so stopping it isn't necessarily best left to software monitoring programs either.
The worst case scenario
In the worst case scenario, a browser hijacker can make the Internet almost impossible to use, popping up legions of advertising windows and directing you helplessly to sites of its choosing. These programs often use a combination of hidden files and a registry settings to reinstall themselves after removal, so deleting them or changing your IE settings back may well not
work.
A much older practice that some shady websites use is to bombard you with advertising popups, some spawning new popup adds when closed, and some lacking any close controls at all, rendering them difficult to get rid of. While this is not technically browser hijacking - it does not affect the functioning of your web browser - it still has the effect of disrupting your surfing experience.
Part 1: preparation and precautions
You can massively reduce the risk of your browser being taken over by a hijacker by taking a few simple precautions. First and foremost is to update Windows by going to http://windowsupdate.microsoft.com . This advice is in every security guide we have ever published, and for good reason.
Microsoft, whatever people might say, is very active in the area of security and is constantly patching and updating program vulnerabilities which allow things like browser hijacking.
By keeping your machine up to date with the latest service packs and patches, you can eliminate a whole range of potential trouble. Many browser hijackers are geared to attack areas of vulnerability in Windows and Internet Explorer which have since been patched. Provided you are up to date, you avoid a raft of potential trouble.

The automatic update function included in Windows XP (and Windows 2000 service pack 3) is a convenient way to make sure you are up to date. To enable this feature, right click on 'my computer' and select properties, then choose the 'automatic updates' tab.
If it is not already, check the 'keep my computer up to date…' checkbox to enable automatic updating.
Now run Windows update from 'start\all programs\windows update' to make sure you are correctly patched for now.
Use common sense
A majority of browser hijacking programs will actually request your permission before installing themselves. If only real hijackers were so polite… Anyhow, the point is if anything requests permission to install on your system while you are browsing the 'net, say NO unless you are absolutely darn sure you know what it is, and what it does.

This excellent surfing habit will also protect you from many forms of spyware and adware such as the omnipresent Gain\Gator\Claria Corporation software.
Funny how many of the same street-proofing techniques you learned as a kid apply on today's Internet… "Kids, just say NO to spyware!"
Use and update an anti-spyware program regularly
Ad-aware and Spybot S&D are the two anti-spyware programs that we recommend using. Since browser hijackers are considered an offshoot of the whole spyware\adware\malware phenomenon, both these programs are capable of detecting and often eliminating our current subject. Keep them updated and scan with them often to keep your PC of unwanted 'marketing initiatives' as well as browser hijackers.
Use Anti-virus programs regularly
Many browser hijackers are also identified and stopped by anti-virus software packages. Running Norton Antivirus with 'auto-protect' enabled is a good idea as a security measure, and there are many other equivalent antivirus programs that can help.
Use antivirus 'auto protection'
Many AV programs come with a program that constantly scans information entering and leaving your computer for viruses and malware. Norton's 'auto-protect' is one example of this. While they can occasionally cause trouble with installing and running software, these programs are your friends when it comes to protecting your PC from browser hijackers and Trojan horse viruses contracted from websites. Make sure your antivirus package has an equivalent feature up and running.
Keep an anti-hijack 'toolkit' for emergencies
There are several free programs available which will help you recover your system in the event of a hijacked browser. Ad-aware and Spybot, which we covered above, are two of them. In addition, download and store Hijackthis and CWShredder. Both of these programs can help you recover in the case of an emergency. A reputable Antivirus program like those provided by Norton, MacAfee or Panda is also essential, as many browser hijackers are considered to be 'Trojan horse' viruses and can be detected and removed by antivirus software.
Change your Internet Explorer security settings
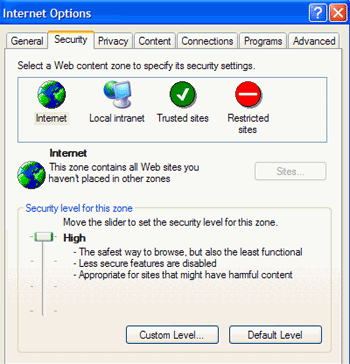
Browser hijacking is one of the web's constant dangers. IE contains some security features which can be used to ward off annoying malware like browser hijackers. Open Internet Explorer, go to the 'tools' menu and select 'Internet options.'
Now select the 'security' tab.
If you want the highest degree of protection against browser hijackers and other malicious online code, set your Internet zone to the 'high' security setting. This will ensure that IE does not run activeX instructions, the means by which most browser hijackers get access to your computer.
Note that this may also cause problems and missing content in some legitimate web pages.
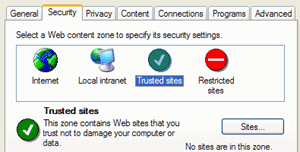
To get around this, you can place trusted websites that you regularly visit into the 'trusted sites' Internet zone.
Site addresses that you enter here will be mostly unrestricted, allowing them to display their content properly.
Try an alternate browser
The best way to defend against many browser hijackers is to stop using Internet Explorer altogether. Since a majority of these programs are coded specifically for IE, switching browsers will render them harmless. Consider Mozilla as one alternative.
Repairing a browser hijack
So your browser is sending you to www.youbuynowdammit.com every time you open it? Can't seem to change it, and obscene ads are popping up all over? Fear not, PCstats is here.
Quick note: Dealing with popup overload
Have you ever mistyped a URL and ended up with a never-ending tide of filthy pop up ads which you frantically attempt to close before your spouse/boss/grandma walks in? If so, you'll be relieved to hear that there is a quick and dirty way to stop this without shutting off the computer or the monitor. On Windows XP or 2000, simply press CTRL+ALT+DEL and go to the 'processes' tab. From here, highlight 'IEXPLORE.EXE' and hit 'end process.' This will close all open IE windows. Now you can reopen the browser in peace.
Fixing a reset Homepage
First of all, try changing your homepage back to its normal setting. This will likely not work, but it's worth a try and will help us to gauge the severity of the problem. From Internet Explorer, go to 'tools\internet options' and change the home page address back to your normal site.
If you have noticed that new entries have been added to your 'favourites' list, remove them by going to 'favourites\organize favourites' and deleting the offending entries. Now restart your computer and reload IE. Are things back to normal? If so, great. If not, read on.
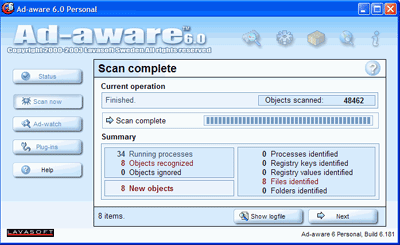
Using Ad-aware
First things first. If you have not already, download and run Ad-aware. Make sure you update the program first via its built in procedure so that you know you are up-to-date. Do a full system scan and make note of any findings, especially processes and registry changes.
Delete all items found by the program, then make sure to empty the recycling bin.
Now restart your computer and run Ad-aware again, with the same procedure. Hopefully you will get a clean bill of health. If so, try your browser again. If everything is back to normal, great.
If not, try setting the home page and deleting any new favourites manually, as detailed above, then restart your system again.
If your browser is not back to normal by this point, or if Ad-aware is still picking up nasty processes and registry entries, it's time to move to the next step.
Antivirus Scan in safe mode
To start an Antivirus scan in safe mode, you first have to ensure that the software has been recently updated with the latest antivirus patch. If that is the case, then restart your system in safe mode.
To do this: Press 'F8' repeatedly immediately after the POST screen, the first screen you see when your computer starts up. This will bring up the Windows boot menu. Select 'boot in safe mode' or the equivalent. Once Windows has loaded in safe mode, do a full system scan with your antivirus software and delete or quarantine any infected files.
Reboot in normal mode and recheck your browser. If all is not well, proceed to the next step.
Manual system search: HOSTS file
If none of the above methods have eliminated your problem, the next step is a manual search through several areas of your system, looking for signs of the offending program. To do this: First go to the control panel and open 'add or remove programs.' Look for any suspicious entries here (software you don't recognize, or which is named oddly or contains links to the problems you are experiencing.) and remove them.
Empty the recycling bin.
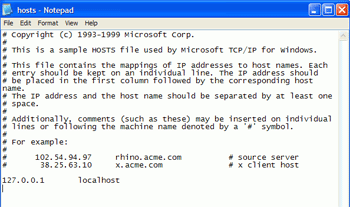
Open the HOSTS file by launching a Notepad window and opening the 'C:\WINDOWS\SYSTEM32\DRIVERS\ETC\HOSTS' file. Note that the HOSTS file has no extension, so it will not appear as a text file. You will need to change the 'files of type' dropdown box to 'all files' in order to see it.
The HOSTS file provides a means for your system to resolve DNS addresses (like www.google.com ) into IP addresses for transferring data across a network or the Internet.
Typing the addresses from the right hand column into your browser will result in it being directed to the IP address to the left of that address. In this way, a browser hijacker can divert traffic automatically from legitimate pages to those of its own choosing, since your computer will check its own HOSTS file for data on an address you enter before it asks your Internet Service Provider's DNS server for information.
The only entry in a normal HOSTS file should be
'127.0.0.1 localhost'
Unless you have customized it yourself or your computer is part of a network which is managed by someone else. Note that in some cases, other programs such as Norton's email protection software may insert their own entries into the hosts file. What you are looking for is a diversion of commonly used websites or Internet Explorer search functions to a specific valid IP address.
The picture above shows a HOSTS file with a foreign entry which would redirect a browser to the IP address '216.177.73.182' if 'www.google.com' was requested. Eliminate any foreign entries and save the file.
Manually Checking the registry
Now let's check the Windows registry.Open the registry editor by going to 'start/run' and typing 'regedit.'
From here, open the 'edit' menu and click 'find.' Now type in the URL of the web page you are redirected to by the browser hijacker. If you find an entry, delete it and press F3 to continue searching through the registry. Delete all matching registry entries, but first make a note of their contents, looking for any keywords. You can do successive registry searches on these words if your problem is not fixed.
Now empty the recycling bin again for luck and restart the computer. Check to see if your problem has gone. If it has not, there are likely settings in the registry which you missed. Try all three manual searches again. Using the above methods should quickly make your browser hijacking a thing of the past.
Now that your computer is clean again, please be careful. Increasingly, the dark corners of the Internet are a dangerous place to surf. Be sensible, follow our tips and keep your guard up. Note that browser-hijacking programs are constantly emerging and changing, just like computer viruses, so it pays to keep your scanning programs updated. Scanning your computer weekly for spyware and viruses is always a great idea too.
Credit to : PCStats










0 comments:
Post a Comment